Those that gone phishing to attack your URL or Website
By darkangel079
@darkangel079 (1488)
United States
January 1, 2008 3:22pm CST
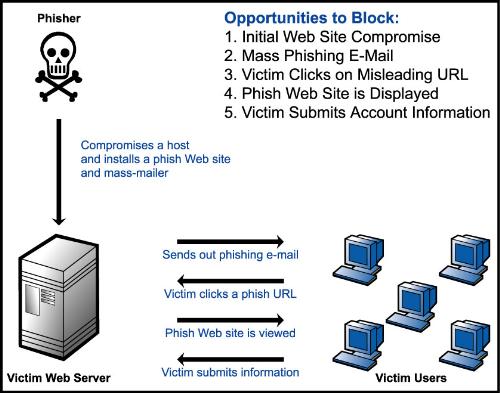
Throughout history the internet has always had issues when it came to security. Programmers, crackers and hackers sit down on their computers to program malicious codes just to manipulate and destroy your data on your own system. We've heard them all - Viruses, Trojan Horses, Spyware, Malware, Adware, Homepage Hijackers and the like. Now in this day and age - They came with a bigger challenge and problem - Phish Attacks - There's an image that I have posted that gives details on how it works. How it works is that an intruder creates a malicious code on your URL/Website so they can retrieve information including stealing your password from that site. This has become a big issue with those that have Myspace, Friendster or other accounts that people use to contact or make friends online. It has happened to many people I know - due to the fact that those that copy or paste certain URL codes don't realize it contains a hack code for those to steal your information. And these are people who are victims from those who steal identities, credit card numbers and many other things. Have you been a victim of an internet phish attack or know someone that had this happen to them?
1 response
@bballchamp1 (194)
• Canada
1 Jan 08
Ive heard of phishing before but never did it seem as relevant as it does now. Im currently working on a website to upload but now that i hear this i have a question. How does a web develeper protect himself/herself from phishing (if they own their own site) and how does someone protect themselves from losing information through phishing.
@darkangel079 (1488)
• United States
1 Jan 08
Since phishing has become a bigger issue in today's security world - they have already developed programs that prevent phishing from happening. Products from Norton, Mcafee and other internet security products. What these programs do is that for example if you go into a website or your own account this protection will ask you if you want to continue your process depending on your own activity - if it detects anything suspicious by an intruder or any malicious code - that program will allow to block it and not enter through.